- A buffer overflow is an anomalous condition where a process attempts to store data beyond the boundaries of a fixed-length buffer
- This may overwrite adjacent memory locations with crucial data and crash the program, have it send incorrect results, or result in other security and privacy breaches
- This is the most common problem in C/C++ programs, but can happen in any program with low level memory access really
- Buffer overflows are one of the most common vulnerabilities
How does memory work? §
Malloc and Memory Management
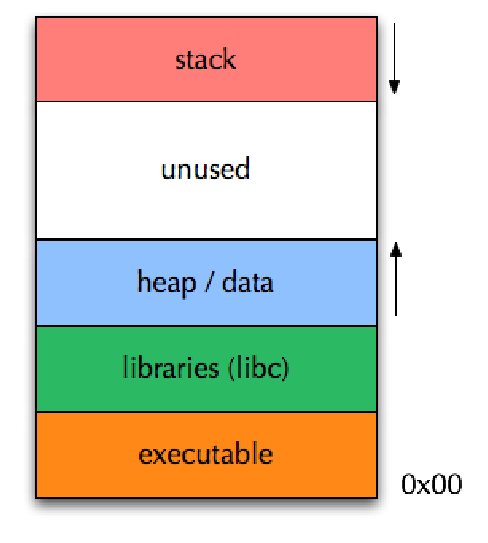
- The memory of a process is divided into 3 regions
- Text: the executable code from the program
- Heap: dynamically allocated ata
- Stack: local variables, function return addresses, stack pointer, continuously grows and shrinks
- The heap grows up, stack grows down
Summary §
- Requires an unsafe function
- strcpy/strcat/strcmp
- gets
- printf/scanf
- memcpy
- Attacker has to be able to control what can go into the buffer and unsafe function
- Buffer must contain address of attack code in return position
- Attacker must know where buffer will be when function is called
