Domain Name System
google.comis easy to remember but not routable- 74.125.228.65 is routable
- Name Resolution: the process of mapping the name to the route
www.cs.purdue.edu= “domain name”www.cs.purdue.eduis a “subdomain” ofcs.purdue.edu- Domain names can map to a set of IP addresses
- For example, google.com maps to many IP addresses
- “zone” = a portion of the DNS namespace, divided up for administrative reasons
- Think of it like a collection of hostname/IP address pairs that happen to be lumped together
- www.google.com, mail.google.com, dev.google.com etc.
- Subdomains do not need to be in the same zone
- Allows the owner of one zone (purdue.edu) to delegate responsibly to another (cs.purdue.edu)
- “nameserver” = a piece of code/a machine that answers queries of the form “What is the IP address for foo.bar.com?”
- Every zone must run >= 2 nameservers. This is for redundancy.
- Several very common nameserver implementations: BIND, PowerDNS (more popular in Europe)
- “authoritative nameserver”
- Every zone has to maintain a file that maps IP addresses and hostnames (”www.cs.purdue.edu is 128.10.19.120”)
- One of the name servers in the zone has the master copy of this file. It is the authority on the mapping.
- “resolver” = while name servers answer queries, resolvers ask queries
- Every OS has a resolver. Typically small and pretty dumb. All it typically does is forward the query to a local…
- “Recursive nameserver” = a nameserver which will do the heavy lifting, issuing queries on behalf of the client resolver until an authoritative answer returns.
- Authoritative nameservers have the lists of mappings. The Recursive nameserver (DNS resolver) actually asks other authoritative servers until it gets a final answer and tells the OS/Browser/requester the IP
- “Record” or “resource record” = usually think of it as a mapping between hostname and IP address
- But more generally, it can map anything to anything
- Many record types
- A records are Address records. Those are the primary ones
- Nameservers within a zone must be able to give:
- Authoritative answers (A) for hostnames in that zone
- Pointers to name servers who host zones in its subdomains
How does DNS work
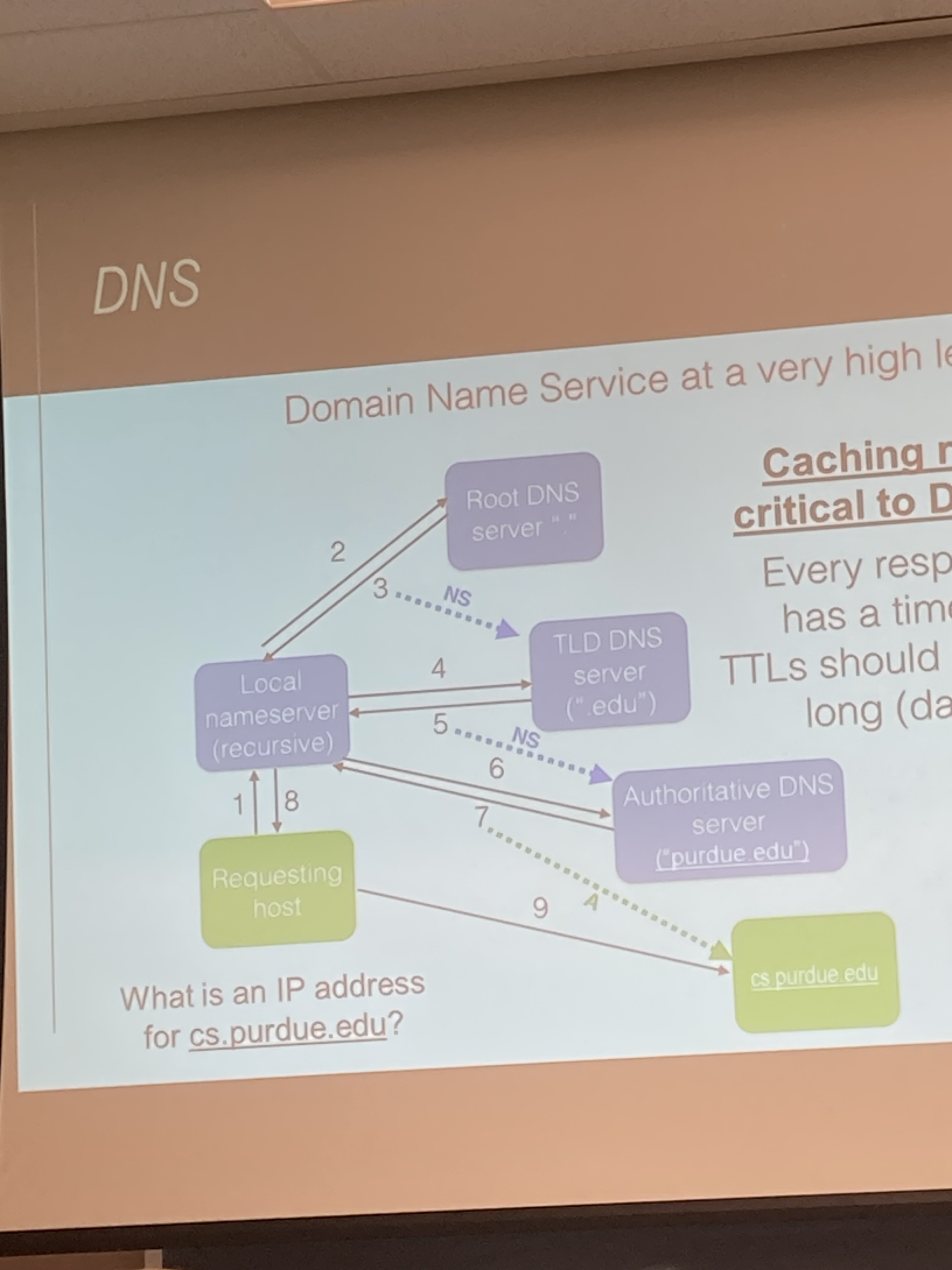 Caching responses is critical to DNS’s success. Every response (3,5,7,8) has a time-to-live (TTL). TTLs should be reasonably long (days), but some are minutes.
Caching responses is critical to DNS’s success. Every response (3,5,7,8) has a time-to-live (TTL). TTLs should be reasonably long (days), but some are minutes.
- How do they know these IP addresses?
- A parent knows its children: part of the registration process
- The root nameserver is hardcoded into the local DNS server (and every DNS server)
- 13 root servers (logically): A root, B root, … M root
- These IP addresses change very infrequently
Caching
- Central to DNS’s success
- Also central to attacks…
- “Cache poisoning”: filling a victim’s cache with false information
- Every query to authoritative name servers have the same request. “What is the IP address for x.y.z?”
- They all have different query ids and different ports
- The local resolver has a lot of incoming and outgoing queries at any point in time
- To determine which response maps to which queries, it uses a query ID
- Query ID: 16 bit field in the DNS header
- Requester sets it to whatever it wants
- Responder must provide the same value in its response
- Query ID’s used to just increment basically
- So if we make a request to the recursive name server for a certain thing, and then guess the query id and respond to the recursive name server BEFORE it gets a response form the authoritative ones, it will use our response and cache it. It will ignore the authority’s answer.